INNSBRUCK, Austria, Oct. 24, 2022 /PRNewswire/ — Windows’ Local Security Authority Subsystem Service (LSASS) is considered one of cybercriminals’ targets when launching focused assaults on an organisation’s community. In this blogpost, we focus on the importance of this course of to focused assaults.
From the angle of an attacker, the LSASS course of on a Windows machine is typically key to getting helpful credentials from area customers, and utilizing them to maneuver laterally throughout the focused community. There are a number of totally different strategies, together with customized-designed malware, that can be utilized by attackers and purple groups to extract credentials from the LSASS course of.
Protection in opposition to LSASS credential dumping Depending on the put in safety product and relevant coverage, it might be simpler or more durable for an attacker to pay money for Windows person credentials by dumping the deal with reminiscence of LSASS.
Some safety merchandise embody particular hardening measures to guard the LSASS course of and forestall credential dumping. However, it could not at all times be doable to make use of these extra restrictive insurance policies in some organisations’ environments, as they could trigger issues with some legacy apps or apps which are not well programmed. Hence, it is advisable for IT directors to check a product’s hardening settings, to see if they’ve any undesirable facet-results.
Furthermore, blue groups ought to nonetheless assume that decided attackers will discover a solution to dump the LSASS course of, even when the put in safety merchandise use particular code to harden the LSASS course of in opposition to assaults. That is to say, they might nonetheless be capable to extract person credentials from the LSASS course of. In addition to the particular LSASS-hardening measures, safety merchandise might forestall credential dumping by way of e.g. the antivirus module; this will detect the malware used, or different recordsdata created by the malware, or use behavioural detection to dam the malicious actions. In some instances, the safety product might not block the assault, however will no less than produce an alert, thus warning the system administrator that the malicious actions needs to be investigated.
Some business safety merchandise have their LSASS hardening measures activated by default. Examples are Avast Ultimate Business Security, Bitdefender GravityZone Business Security Enterprise, and Kaspersky Endpoint Detection and Response Expert. Microsoft additionally gives two options particularly used to guard the LSASS course of, specifically PPL (Protected Process Light) and ASR (assault floor discount) guidelines. PPL is enabled by default on Windows 11, however at present not on Windows 10; it is included within the Professional, Enterprise and Education variants of Windows 10/11. The ASR guidelines can be utilized in organisations’ networks together with Microsoft Defender, and at present should be proactively configured on both OS.
Test of credential-dumping safety in safety merchandise
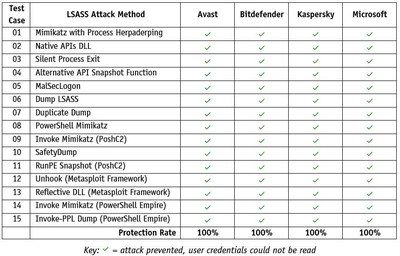
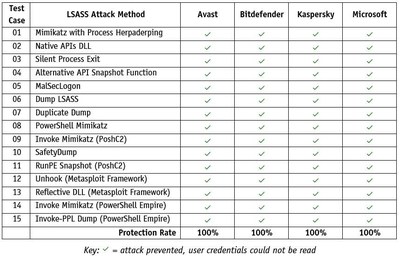
Given the significance of stopping LSASS credential dumping, in May 2022 AV-Comparatives tried out some business safety merchandise to find out how well their hardening measures protected in opposition to assaults on LSASS.
Below we record some examples of merchandise (made by Avast, Bitdefender, Kaspersky and Microsoft) that confirmed efficient safety in opposition to the 15 assaults utilized in our take a look at, with their respective LSASS hardening measures enabled.
The desk above contains outcomes for the next merchandise (with LSASS safety settings enabled): Avast Ultimate Business Security, Bitdefender GravityZone Business Security Enterprise, Kaspersky Endpoint Detection and Response Expert and Microsoft Defender for Endpoint.
Microsoft requested us to publish the outcomes of a further take a look at of Microsoft Defender for Endpoint that we ran with out their LSASS safety options (PPL and ASR) enabled. This was carried out to find out if the assaults listed above can be detected by different Microsoft safety features. For every take a look at case, AV-Comparatives checked to see if the assault was appropriately attributed to the MITRE ATT&CK techniques and strategies with regard to LSASS within the case of detections or lively alerts by the safety product. In instances the place the assault was prevented by the safety product, the lab checked to see which details about the menace was supplied within the admin console. The methodology and different particulars of this take a look at will be discovered on this PDF. For extra data, please learn additionally this weblog entry from Microsoft.
E-mail: [email protected]
Phone: +43 720115542
Contact: Peter Stelzhammer
Photo – https://mma.prnewswire.com/media/1927734/AV_Comparatives_LSASS_Table_Infographic.jpg
Logo – https://mma.prnewswire.com/media/1867361/AVC_Logo.jpg

![]() View authentic content material:https://www.prnewswire.co.uk/news-releases/av-comparatives-takes-a-deep-dive-into-lsass-security–not-all-is-well-301657142.html
View authentic content material:https://www.prnewswire.co.uk/news-releases/av-comparatives-takes-a-deep-dive-into-lsass-security–not-all-is-well-301657142.html